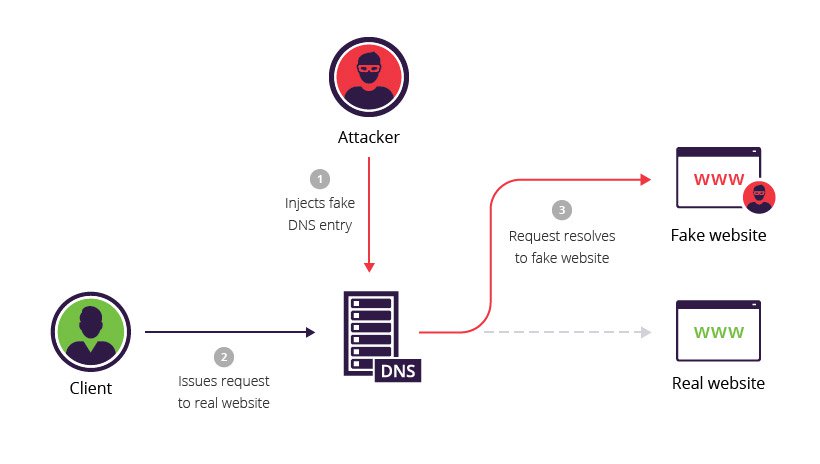
Domain Name Server (DNS) spoofing, or DNS cache poisoning, is an attack involving manipulating DNS records to redirect users toward a fraudulent, malicious website that may resemble the user’s intended destination.
Once on the fraudulent site, users are deceived into logging in to what they believe is their genuine account, thereby enabling the attacker to steal access credentials or other sensitive information. The fraudulent website can install worms or viruses on the user’s computer secretively, giving the attacker sustained access to the user’s device and data.
DNS spoofing works by exploiting flaws in the DNS and its associated protocols. An attack can be accomplished in several ways:
DNS spoofing enables the attacker to steal sensitive data from unsuspecting users. Through a worm or virus, if the attacker gains access to a user’s device, they can leverage this to install ransomware. By redirecting traffic away from legitimate websites and towards their fraudulent site, attackers can increase site authority and search ranking, helping to generate more site traffic to the fraudulent domain in the future.
In a standard DNS communication process, the user’s device initiates a query when the user requests a website. The DNS resolver receives this query, typically operated by the user’s Internet Service Provider (ISP). If the resolver does not have the associated IP address stored in its cache, it will forward the query to a root server. The root server will then direct the resolver to the appropriate Top-Level Domain (TLD) server (e.g., .com, .org, .net). The TLD server will then direct the DNS resolver to the domain’s name server, which returns the corresponding IP address to the resolver. The resolver then provides the IP address to the user’s device, allowing the device to connect to the desired website.
This process is integral to internet navigation, enabling users to access websites using human-friendly domain names rather than numeric IP addresses.
This method involves intercepting communications between users and a DNS server to redirect them to a different or malicious IP address. By positioning themselves between the user and the DNS server, attackers can manipulate the DNS responses and lead users to unintended destinations.
In this method, attackers hijack a DNS server configured to return a malicious IP address. By compromising the DNS server, they gain control over the DNS resolution process and can manipulate the responses to redirect users to malicious sites.
This method exploits the DNS server cache’s Time-To-Live (TTL) values. Attackers manipulate the TTL values to ensure incorrect DNS entries persist for more extended periods. By doing so, they increase the number of potential victims and prolong the duration of the attack. Even users who were not initially targeted can be redirected to malicious sites if the corrupt DNS responses remain in the cache.
Each method poses a significant threat to the integrity and security of DNS resolution, highlighting the importance of implementing robust defenses against DNS spoofing attacks.

DNS server compromise attack.
The following scenario illustrates a DNS cache poisoning attack. In this attack, an attacker (IP 192.168.3.300) intercepts the communication channel between a client (IP 192.168.1.100) and a server computer belonging to the website www.estores.com (IP 192.168.2.200).
To carry out this attack, the attacker employs a tool, like arpspoof, to deceive the client into believing that the server IP is 192.168.3.300. Simultaneously, the server is tricked into thinking that the client’s IP is also 192.168.3.300.
Below is a scenario of how the attack proceeds:
See how Imperva DDoS Protection can help you with DNS spoofing attacks.
Below are several methods for preventing DNS spoofing attacks:
DNSSEC is a suite of specifications for securing certain kinds of information provided by DNS. It gives origin authentication of DNS data, data integrity, and authenticated denial of existence. DNSSEC does not provide confidentiality of data; all DNSSEC responses are authenticated but not encrypted.
Using a trustworthy DNS server can safeguard against DNS spoofing. These servers have highly secure and regularly updated systems that are less likely to be compromised.
Cryptographically secure your communication with DNS servers using protocols like DNSCrypt. This ensures that the responses are from a trusted source and have not been tampered.
Periodic system updates can protect against many types of attacks. Keeping DNS software up-to-date ensures the latest security patches are in place.
Implementing network security measures like web application firewalls (WAF), intrusion detection systems (IDS), or intrusion prevention systems (IPS) can help identify and block potential DNS spoofing attacks.
IPSec uses cryptographic security services to protect communications over IP networks. It enhances and secures data flow between the host and network, or between networks.
Implementing these measures can significantly reduce the risk of falling victim to a DNS spoofing attack. However, it’s important to remember that no single method can provide total protection. A combination of multiple strategies is the best approach.